Understanding Surrogate Models in EDR and XDR: Enhancing Cybersecurity with Interpretability
ATLAN TEAM
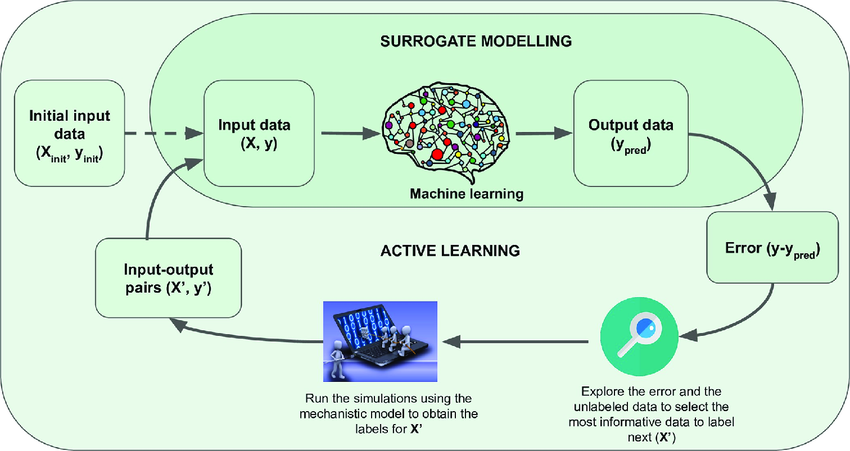
What is a Surrogate Model?
A surrogate model is a simplified version of a more complex model, used to interpret and explain its behavior. In machine learning and artificial intelligence, surrogate models are often employed to make the predictions of complex algorithms more understandable. They provide human-readable explanations, such as decision trees or rule sets, that approximate the decision-making process of the original model. This is particularly useful in domains like cybersecurity, where transparency and interpretability are essential for validating and improving threat detection systems.
EDR: Endpoint Detection and Response
The Role of EDR in Cybersecurity
EDR systems are designed to monitor and respond to threats specifically at the endpoint level. They collect and analyze data from endpoints such as laptops, desktops, and servers to detect suspicious activities and provide detailed forensic insights. This helps security teams to identify, investigate, and mitigate threats effectively.
How Surrogate Models Enhance EDR
In EDR systems, surrogate models can play a crucial role by simplifying the interpretation of complex threat detection algorithms. For instance, an EDR system might use machine learning models to detect anomalies in endpoint behavior that indicate potential threats. However, these models can be opaque, making it difficult for security analysts to understand why certain activities were flagged as suspicious.
Surrogate models address this issue by translating the complex detection algorithms into more intuitive formats, such as decision trees or rule-based systems. This not only enhances transparency but also helps security analysts validate the automated threat detection processes. By providing clear and understandable explanations, surrogate models enable analysts to verify the accuracy of detections, identify false positives, and refine the security measures accordingly (SentinelOne) (Palo Alto Networks).
XDR: Extended Detection and Response
Expanding the Scope of Detection
XDR represents the evolution of EDR, extending its capabilities to provide comprehensive threat detection and response across multiple security layers. Unlike EDR, which focuses solely on endpoints, XDR aggregates and correlates data from various sources, including networks, cloud environments, and email systems. This holistic approach allows for a more comprehensive view of the organization's security posture and enables faster, more accurate threat detection and response.
Surrogate Models in XDR
Given the broader scope of XDR, the complexity of the data and algorithms involved is significantly higher. Surrogate models in XDR help simplify this complexity by providing human-readable explanations for the sophisticated threat detection and correlation processes.
For example, an XDR system might correlate data from endpoint, network, and cloud sources to identify a multi-vector attack. The original algorithms used for this correlation can be complex and difficult to interpret. Surrogate models can translate these complex processes into more accessible formats, making it easier for security teams to understand the nature and context of threats. This improved interpretability not only aids in faster decision-making but also enhances the overall effectiveness of the XDR system by allowing for continuous validation and refinement of the underlying models (Splunk) (Palo Alto Networks).
Benefits of Surrogate Models in EDR and XDR
Improved Interpretability: Surrogate models enhance the interpretability of complex threat detection algorithms, making it easier for security professionals to understand and trust the automated processes. This transparency is crucial for validating detections and ensuring that the system is functioning correctly.
Enhanced Validation and Refinement: By providing clear and understandable explanations, surrogate models enable continuous validation and improvement of the underlying models. Security teams can use these simplified representations to identify false positives, adjust detection thresholds, and refine the security measures to better address evolving threats.
Faster and More Accurate Response: In both EDR and XDR systems, surrogate models facilitate quicker decision-making by providing actionable insights in a more accessible format. This enables security teams to respond to threats more efficiently, reducing the time to detect and mitigate potential attacks.
Increased Trust and Adoption: The transparency provided by surrogate models can increase trust in automated threat detection systems. When security professionals can understand and validate the decisions made by these systems, they are more likely to adopt and rely on them for their cybersecurity needs.
Challenges and Considerations
While surrogate models offer significant benefits, there are also challenges and considerations to keep in mind:
Balancing Accuracy and Simplicity: Creating a surrogate model involves simplifying the original model, which can sometimes lead to a loss of accuracy. It is essential to strike a balance between simplicity and the fidelity of the surrogate model to ensure that it accurately represents the behavior of the original model.
Maintaining Up-to-Date Models: As threat landscapes evolve, the underlying models in EDR and XDR systems need to be continuously updated. Surrogate models must also be updated accordingly to ensure that they remain accurate and relevant.
Integration with Existing Workflows: Implementing surrogate models requires integration with existing security workflows and tools. This can be a complex process, especially in organizations with limited resources and expertise. It is important to consider the integration challenges and plan accordingly to ensure a smooth implementation.
Future Outlook
The use of surrogate models in EDR and XDR systems is likely to grow as the demand for interpretability and transparency in cybersecurity continues to increase. Advances in machine learning and artificial intelligence will further enhance the capabilities of surrogate models, making them more accurate and easier to implement.
As organizations strive to improve their security posture, the ability to understand and trust the decisions made by automated threat detection systems will become increasingly important. Surrogate models will play a crucial role in achieving this goal, providing the transparency and validation needed to ensure the effectiveness and reliability of EDR and XDR systems.
To summarise, surrogate models offer a powerful tool for enhancing the interpretability, validation, and effectiveness of EDR and XDR systems. By simplifying complex algorithms and providing human-readable explanations, they help security professionals understand, trust, and improve automated threat detection processes. As cybersecurity threats continue to evolve, the use of surrogate models will be essential in ensuring that advanced detection systems remain accurate, transparent, and effective.