Exploitation of Vulnerabilities: A Topic-Based Machine Learning Framework for Explaining and Predicting Exploitation
ATLAN TEAM
Authors: Konstantinos Charmanas, Nikolaos Mittas, Lefteris Angelis
Published in: Information, 2023
DOI: 10.3390/info14070403
Introduction
The paper addresses the critical issue of security vulnerabilities in software and hardware, which can lead to severe damage if exploited. The study emphasizes the importance of prioritizing vulnerabilities to develop effective countermeasures. It proposes a machine learning framework that uses topic distributions derived from word clustering in vulnerability descriptions to predict the likelihood of exploitation.
Key Contributions
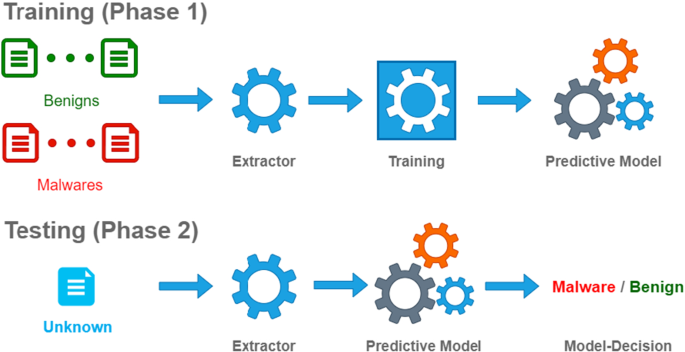
- Topic-Based Framework: The authors introduce a framework that maps newly disclosed vulnerabilities to topic distributions through word clustering. This mapping helps predict whether a new vulnerability will have an associated exploit Proof of Concept (POC).
- Generalized Linear Model (GLM): The study employs a GLM to link topic memberships of vulnerabilities with exploit indicators, identifying five topics frequently associated with recent exploits.
- Improved Topic Coherence: The proposed method significantly improves topic coherence in LDA models by up to 55% and achieves an accuracy of nearly 87% in classifying vulnerabilities as exploitable or not.
- Practical Insights: The research provides guidelines on the relationships between the textual details of vulnerabilities and potential exploits, aiding in the prioritization of security threats.
Methodology
- Data Collection: Vulnerability descriptions are collected from the National Vulnerability Database (NVD) and associated with exploit indicators from ExploitDB.
- Word Representation: The study uses Global Vectors (GloVe) for word representation, which is effective in document classification tasks.
- Dimensionality Reduction: Uniform Manifold Approximation and Projection (UMAP) is used to project word representations into a two-dimensional space, facilitating clustering.
- Clustering: The Fuzzy K-Means algorithm (FKM) is applied to identify clusters of keywords and assign topic memberships to vulnerabilities.
- Classification Models: The topic memberships are used to train machine learning models to predict the exploitability of new vulnerabilities. The models are compared with baseline algorithms like LDA and CTM.
Results
- Topic Extraction: The framework successfully extracts interpretable topics and improves topic coherence.
- Classification Performance: The proposed model outperforms traditional topic modeling algorithms in predicting exploitability.
- Practical Application: The framework can be trained and reproduced for different periods, making it a versatile tool for proactive vulnerability management.
The paper reviews previous studies on vulnerability exploitation, highlighting the importance of multiple data sources for accurate prediction. It discusses various text mining and machine learning techniques used in the field, emphasizing the novelty of using topic-based approaches for vulnerability prioritization.
The study presents a robust framework for predicting the exploitation of vulnerabilities using topic-based machine learning techniques. The proposed method enhances the accuracy of vulnerability assessment and provides actionable insights for cybersecurity professionals. Future work includes refining the framework and exploring additional data sources to improve prediction capabilities.
Keywords
- Text mining
- Exploits
- Fuzzy clustering
- Topic extraction
- Security vulnerabilities
- Machine learning
This detailed summary encapsulates the key aspects of the paper, including its methodology, findings, and significance in the field of cybersecurity.