Summarizing the Paper "Classification and Online Clustering of Zero-Day Malware"
ATLAN TEAM
Summarizing the Paper "Classification and Online Clustering of Zero-Day Malware"
Introduction: The Ever-Growing Threat of Malware
Malware continues to pose significant threats to cybersecurity. Encompassing various forms such as viruses, trojans, bots, worms, backdoors, spyware, and ransomware, malware's prevalence is ever-increasing. According to the AV-Test Institute, approximately 560,000 new malware samples are detected daily. The sheer volume necessitates automated methods for malware detection and classification to efficiently manage and mitigate these threats.
Understanding Malware Detection and Classification
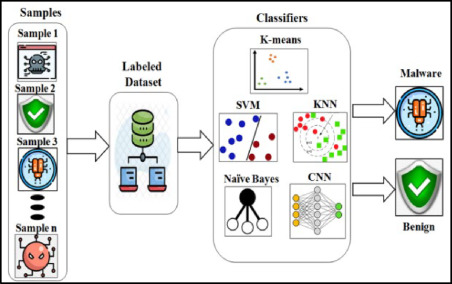
Malware detection techniques typically fall into two categories: signature-based and anomaly-detection techniques. Signature-based methods rely on predefined signatures (specific sequences of bytes in malware code) to identify threats. However, these methods struggle to detect zero-day malware—new threats with no existing signatures. Anomaly-detection methods, leveraging machine learning, analyze behavioral patterns to identify malware, offering a more adaptive approach but often with higher false positive rates.
The Role of Machine Learning in Malware Analysis
Machine learning has revolutionized malware analysis through methods like static analysis, dynamic analysis, and hybrid analysis. Static analysis inspects malware without execution, while dynamic analysis observes behavior during execution in a controlled environment. Hybrid analysis combines both methods to extract comprehensive feature sets.
Classification and Clustering of Malware
Malware classification involves assigning malware samples to known families based on their characteristics. Conversely, malware clustering groups unlabeled data into clusters based on similarity, aiding in the identification of new, previously unknown malware families. This paper focuses on an innovative system designed to classify and cluster zero-day malware in real-time.
Proposed System: Online Processing of Zero-Day Malware
The authors propose a novel system for the online classification and clustering of zero-day malware. Utilizing a multilayer perceptron (MLP) for classification, the system assigns known malware samples to existing families. When new, unfamiliar samples are encountered, they are clustered using self-organizing maps (SOMs).
Key Contributions and Methodology
Architecture Design: The proposed system is designed to handle real-time processing of over 560,000 samples daily. It efficiently classifies known malware and clusters new samples into emerging families.
Experimental Setup: The authors utilized the EMBER dataset, featuring static analysis-derived attributes from portable executable files for the Windows OS. The dataset included seven prevalent malware families, with four in the training set and three additional families in the test set.
Classification and Clustering Results: The system achieved a classification accuracy of 97.21% with a balanced accuracy of 95.33%. For clustering, the SOM method produced purity ranging from 47.61% to 77.68%, depending on the number of clusters.
Detailed Process Overview
Data Extraction and Preparation: Features were extracted from malware samples using static analysis. These features formed the basis for the classification and clustering processes.
Classification Using MLP: The MLP classifier assigned known malware samples to existing families based on learned patterns.
Clustering with SOM: Unclassified samples were clustered using SOM, allowing the identification of new malware families. This method leverages topological properties to map high-dimensional data into clusters.
Evaluation and Results
The system demonstrated robust performance, effectively managing the high volume of daily malware samples. The classification accuracy of 97.21% and balanced accuracy of 95.33% underscore its efficacy. Clustering results, with purity up to 77.68%, indicate significant potential for identifying new malware families.
Conclusion and Future Work
The proposed system marks a substantial advancement in the automated classification and clustering of zero-day malware. Future work will likely focus on refining clustering algorithms and integrating dynamic analysis features to enhance detection capabilities further.
This detailed blog post aims to provide a comprehensive overview of the innovative approaches in the paper "Classification and Online Clustering of Zero-Day Malware," highlighting the system's design, methodology, and significant contributions to malware detection and classification.