Outrunning Windows Kernel Notification Routines from User-Mode: Explained
ATLAN TEAM
Introduction
In today's digital age, security is paramount, especially for operating systems that form the backbone of our computing experience. One such system, Microsoft Windows, was discovered to have a significant security flaw. This post aims to explain this flaw in simple terms and discuss its implications and possible solutions.
What is the Flaw?
The flaw is a fundamental design issue within Microsoft Windows operating systems (OS), affecting versions such as Windows 7 and Windows 10. This flaw allows unprivileged user-mode processes (the programs you typically use) to bypass security protections set by the Windows kernel (the core part of the OS that manages system operations).
How Does the Flaw Work?
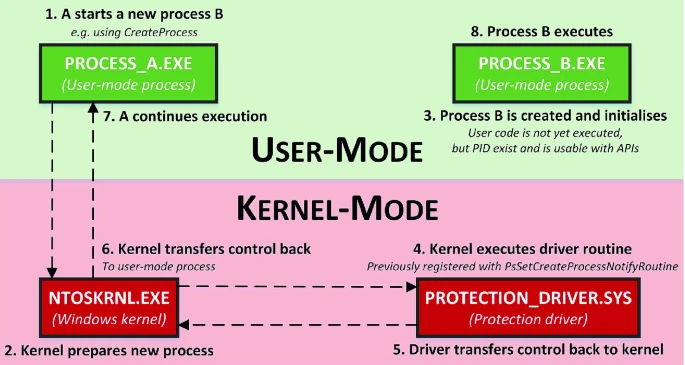
Normally, when a process (a running program) starts, Windows uses something called "notification routines" to set up security protections. These routines are supposed to ensure that sensitive processes, like anti-virus programs or system utilities, are protected from being tampered with by other less-privileged processes.
However, researchers found that it's possible for a user-mode process to "outrun" these notification routines. This means that an unprivileged process can gain access to other processes before the security protections are applied. Essentially, there's a window of time during which the protections aren't yet in place, and malicious programs can exploit this gap.
Real-World Impact
To understand the impact, consider several key applications:
Anti-Malware Software: Programs like Symantec Endpoint Protection rely on these kernel routines to protect themselves from being disabled by malware. If malware can bypass these protections, it can effectively neutralize anti-virus software, leaving the system vulnerable.
Virtualization Software: VirtualBox, used for running virtual machines, also depends on these security measures. An exploit here could lead to unauthorized access to virtual machines, compromising their security.
Video Game Anti-Cheat Systems: Games protected by anti-cheat software like BattlEye and EasyAntiCheat could be compromised, allowing cheats to manipulate game processes undetected.
Response and Solutions
Upon discovering this flaw, researchers disclosed it to Microsoft. While Microsoft acknowledged the issue, they decided not to issue an OS patch, citing potential compatibility issues as a concern. Instead, application developers have been left to implement their own fixes, which vary widely and may not cover all scenarios.
Proposed Solutions
Several potential solutions were discussed, though each has its challenges:
Kernel-Space Respawn: One solution is to terminate and restart the protected process from the kernel space immediately upon detection, ensuring security protections are applied from the get-go. However, this requires specialized knowledge and is not feasible for all applications.
Handle Invalidation: Another approach is to invalidate any handles (a type of reference to system resources) obtained during the vulnerable period. This means that even if a malicious process gains temporary access, it would lose it quickly. Again, this isn't universally applicable and comes with its own set of challenges.
API Changes: The most comprehensive solution would be for Microsoft to change how their APIs handle process initialization, but this could lead to widespread compatibility issues, affecting many existing applications.
This security flaw in Windows highlights a delicate balance between maintaining compatibility and ensuring security. While individual fixes by application developers provide some level of protection, a more unified approach from Microsoft would be ideal, though challenging. This example underscores the complexity of OS-level security and the continuous effort required to safeguard our digital environments.
For those interested in the technical details, the researchers have made their findings and related resources available on platforms like GitHub, providing valuable tools for developers to test and enhance their security measures.